As you have likely heard in the news, the Toronto Transit Commission, Newfoundland Health Care Network and Saskatoon Health Care Network were all recently attacked by ransomer. These attacks brought down a large portion of their networks and disabled important services.
It is important for your business safety to help users understand how to identify suspicious emails and how best to respond should your system become infected. Your best defence is an educated work force.
How is your Network Protected
Your site is set-up and designed to limit outside connections – best practices say to restrict outside access to ONE connection that can be watched and managed. That would be your router – and it is watched and managed.
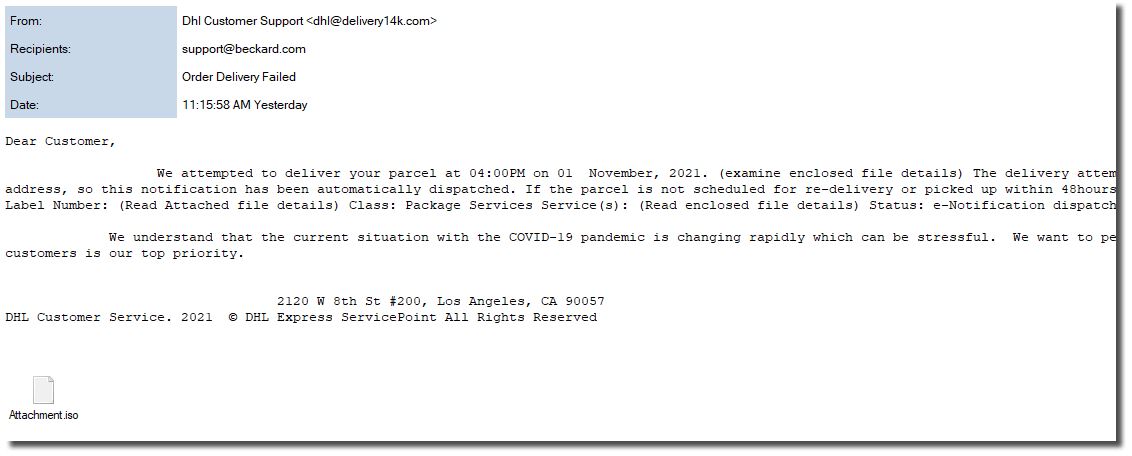
The big risk that all companies face today is email. This is how ransom ware is typically spread over the internet.
A PC user will get an email that looks real and may include logos or information that is specific to your business operations. It may include an attachment or a link to click.
That is all that is needed to have ransom ware download to that PC and then start to spread over all the mapped drives and connections where that PC user has access. It is that easy.
Again, your best defence is knowledgeable users.
I encourage you to remind staff NOT TO OPEN ATTACHMENTS in emails from an outside source. As well, they should NOT CLICK ON HYPERLINKS in emails from outside domains. These are the main avenues for downloading ransomware code into your network
Canadian Government Cyber Security Centre
Follow the guidelines put forward by Canadian Government Cyber Security Centre and always be cautious in mail… if you’re unsure, don’t click it !
You can always call that company and get confirmation that they sent that email. You can read more from the Canadian Government Cyber Security Centre
How do Businesses Recover After an Attack
Should your network be infected by a virus you want to try and limit the spread.
Turn OFF all computers and network hardware.
Maybe even trip the main breaker for the building. You want to limit the virus moving around to more and more devices.
You should also shutdown your server – even if that means pressing and holding the power button (Crash the server).
Once everything is shutdown, the virus is unable to spread further. Call us and we can work with you to assess the damage.
The Recovery Process
PC’s have a restore point that can be used to restore your affected PC.
https://www.windowscentral.com/how-use-system-restore-windows-10
As well, the server can be restarted in SAFE MODE – SINGLE USER and scanned. This will help identify infected areas of the server. Your backup is then used to over write any of the infected areas of the server storage.
Conclusion – An ounce of Prevention is worth a Pound of Cure
Yes, none of this sounds like fun. Much better to help staff understand the risks. Use caution while in email and avoid downloading these viruses.
If you have any questions – please let us know. We are here to help.
Work Safe